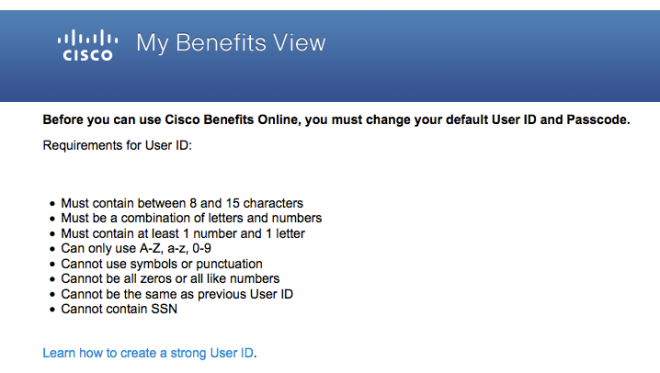
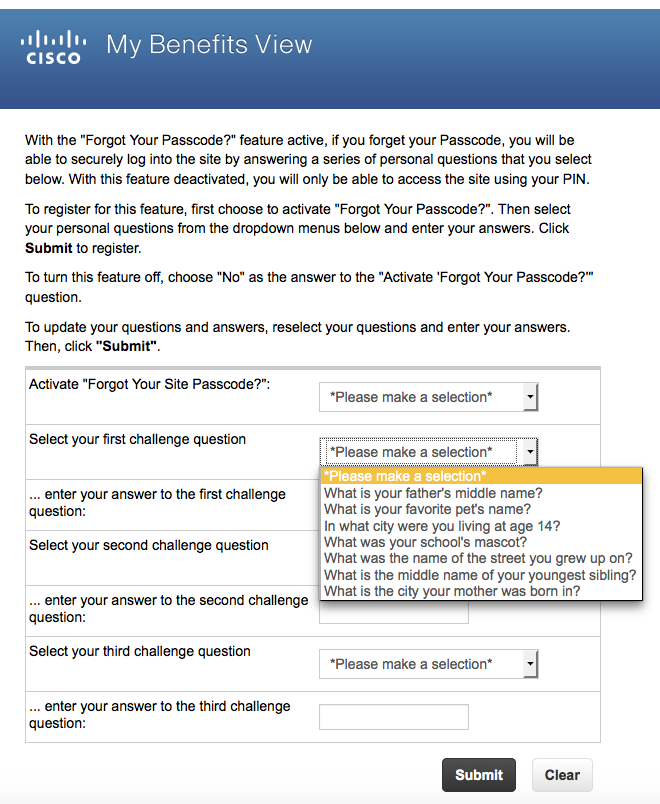
Today, while trying to retrieve an invoice for a medical test, I was subjected to the Cisco Registered Envelope Service (CRES). The message I got from the testing company contained an HTML file, that when I opened it in my browser provided a button to register with CRES. I groaned when it asked me to enter my name and to choose a new password, but I had heard about CRES before and I expected that. I didn’t expect what followed:
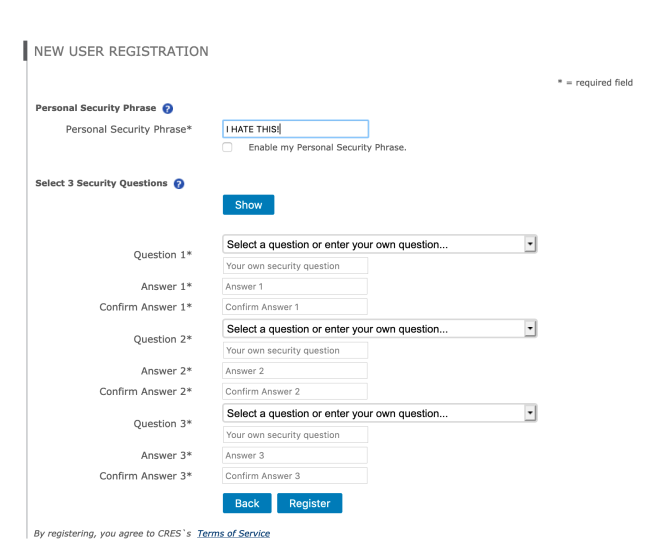
The Personal Security Phrase is apparently something that can be displayed when you’re asked to log in; as you can see I have already filled mine in. I guess this gives users some confidence that they’re not connecting to an impostor site, but it provides little actual assurance because users won’t remember to check this, and the site has TLS certificates anyway.
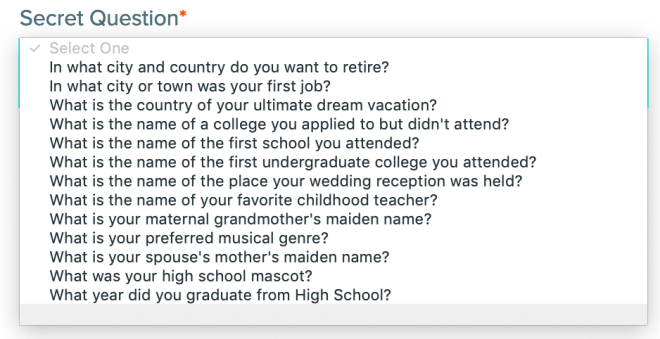
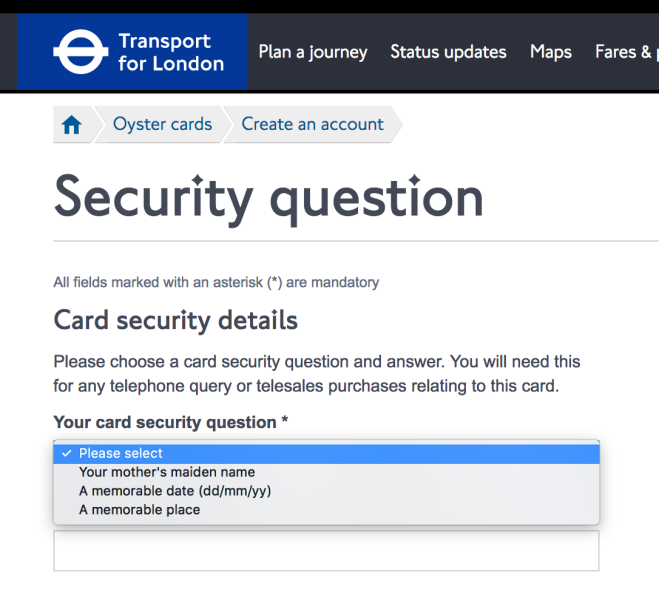
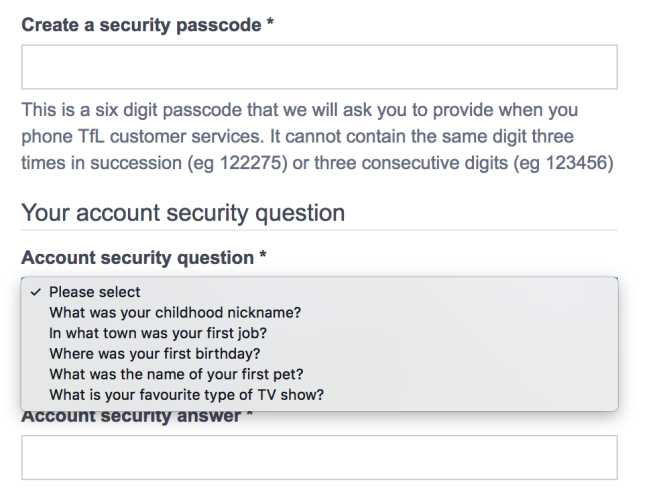
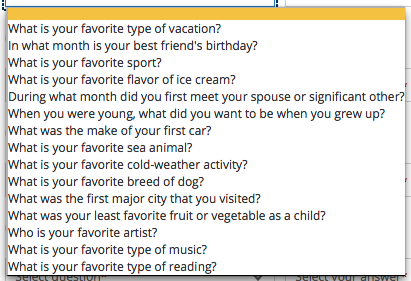
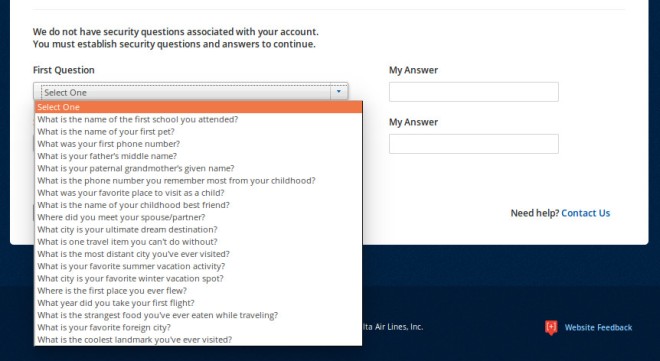
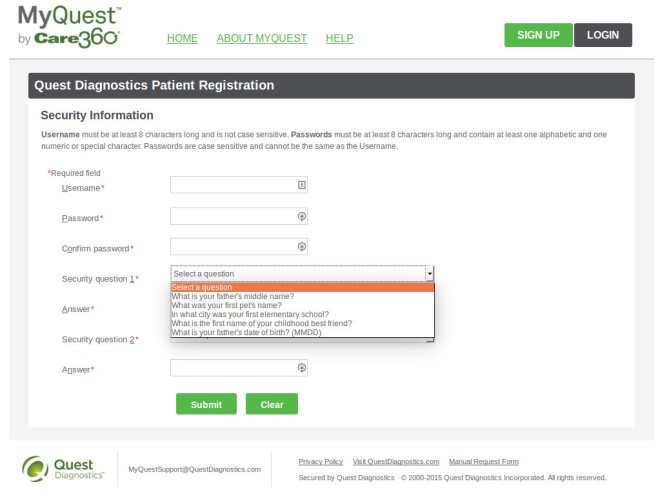
But then: three [in]Security Questions!! The suggested questions are fairly standard, and common to all three question instances:

At least the questions aren’t obviously things (like your high school mascot) that can commonly be found on Facebook. But many of these answers have imprecise answers (e.g., TWA vs. Trans World Airlines), so I wonder how well these can actually be used to authenticate anyone.
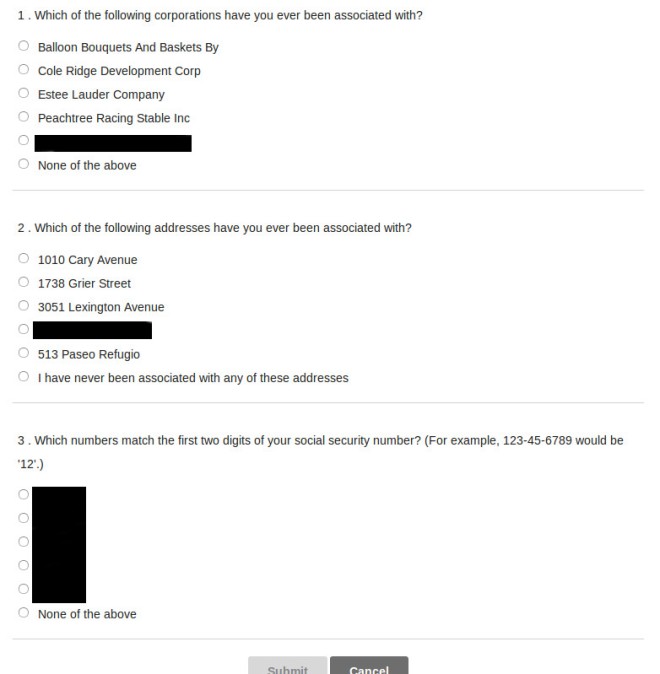
But the other choice is to supply your own question, and people make bad choices when given this option because they don’t consider how easy it is for an attacker to find out the answer. So they might ask what town they live in, or their mother-in-law’s name. This is very poor practice (as if the use of security questions isn’t already).
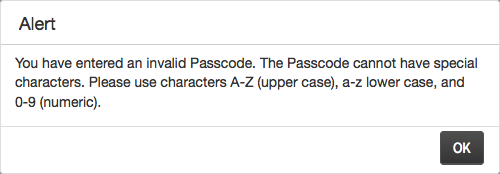
Then we get to the Kafka-esque part. The answers that you type are replaced by dots (like passwords), so it’s easy to make a typing mistake and not have them match. If you make this mistake and press Register, it tells you that the answers didn’t match and clears the form. So you have to start all over and hope you typed all the answers correctly. But in my case, I forgot to re-enter one of the self-supplied security questions and — you guessed it — the form got cleared again. So I had to go through this a third time.
When I finally made it through this form, it emailed me a link to activate my account, and then finally I could log in (username and password, no 2-factor options available) to retrieve my email message. And I finally got my invoice.
I vaguely remember CRES being introduced while I was still at Cisco (2011 or before). As I remember the vision was that we’d get a lot of consumers signing up to get their “secure” email and then we’d have a huge user base that could be leveraged by other collaboration products. But the whole premise behind CRES is flawed — sending someone an email to get them to register to receive another email doesn’t do anything to prevent an impostor from registering. While there are other features like message recall, the main selling point for CRES is message confidentiality, and that isn’t achieved here, at least for the first message.
I’m amazed that this product has lived this long at Cisco.